May 1, 2020 — David Martinez, Security Practice Director at Technologent, was recently quoted in an article for TechTarget.com. Martinez details how companies now face sophisticated enemies using AI and machine learning tools for their attacks. It's a world of new dangers for those defending network systems and data.
Read through the full article here: https://searchsecurity.techtarget.com/feature/AI-powered-cyberattacks-force-change-to-network-security
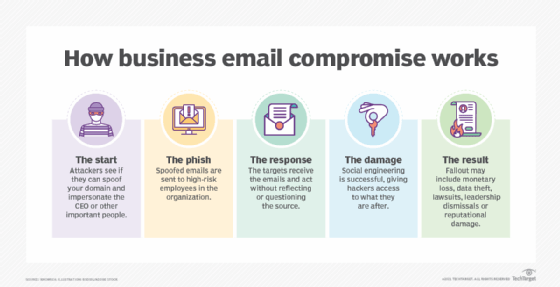
When the manager of a company's U.K. subsidiary got a call in March 2019, he recognized the voice of his Germany-based CEO on the other end of the line. They'd met before, at meetings. The manager gave little thought when the chief requested that he transfer €220,000 to a Hungarian vendor.
"This guy was absolutely sure that this was a call from the German CEO, so he paid the money," said Ruediger Kirsch, a fraud expert with insurance firm Euler Hermes, which underwrote the cyberinsurance policy for the firms involved.
It wasn't until the German CEO called two days later, requesting another €100,000 that the head of the UK subsidiary noticed that, this time, the phone number wasn't the right one -- it came from Austria. So he reached out to the CEO and discovered the executive had no knowledge of either of these transfers. Now worried, he called the number from which the original request came.
"The UK manager said, even when he talked to [the person on the other end] a third time, he was sure it was the voice of the CEO," said Kirsch, who declined to name the companies involved to protect client confidentiality.
In what investigators at Euler Hermes and the companies involved consider the first case of an audio filter used to imitate an executive's voice for "fake president" fraud -- the European name for business e-mail compromise and social engineering -- the criminals made off with the initial €220,000 (about U.S. $240,000).
Welcome to the new world of advanced IT network cybersecurity threats.
Companies have started implementing data and network security basics, with just about every firm protecting the perimeters with firewalls, securing endpoints with host-based security and attempting to detect threats on the fly with web filtering. Attackers have found ways to modify traditional attacks and insert themselves into trusted parts of the infrastructure. As a result, companies can no longer just focus on network security basics, but need to be prepared for more pernicious advanced threats, including deepfakes and AI-powered cyberattacks. In some cases, that's AI-powered fraud, such as the audio deepfake used to mimic the German CEO's voice. In other cases, attackers are sneaking in through suppliers' systems or modifying ransomware attacks to not only steal data but to apply more pressure on companies to pay.
That means companies' defenses need to evolve as well.
"These attackers are finding a way to be more successful," said Dan Basile, executive director of the security operations center for Texas A&M University System (TAMUS). "Almost every company has seen the fake invoices, the fake [requests for proposal]. ... So the attackers are getting better, more impressive and more accurate."
Network security threats target weakness, chaos
Since many companies have developed more mature security measures to defend against AI-powered cyberattacks and other advanced threats, attackers are focusing on smaller, less security-savvy prey, Basile said.
Smaller organizations without a dedicated security team have more trouble keeping up with the latest attacks, he said. Texas A&M and other organizations responded to the concerted ransomware attacks on Texas local government agencies in August 2019. For the most part, local government groups had no security expert and had relied on a managed service provider for their IT security, which left them as easy prey for ransomware attackers.
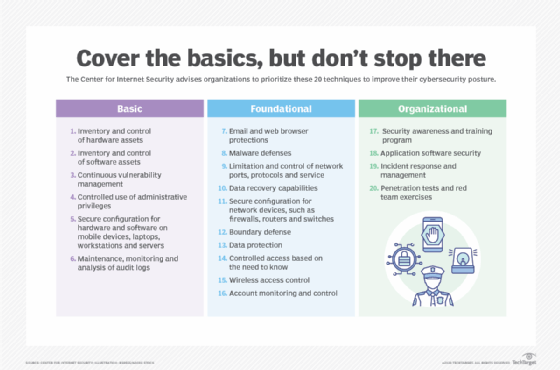
"These groups are actively attacking networks left, right and center -- they are often targeting the smaller organizations that don't have a full-fledged security team," Basile said. "For most companies, even large ones, if they can nail the top two or three elements of the [Center for Internet Security] top-20 list, they are doing well."
Meanwhile, attackers are segmenting their expertise, focusing on specific problems and on selling cybercriminals tools and data on victims to other attackers. Most of the recent attacks Basile has had to deal with are ransomware for hire, he said. And attackers have now combined crypto-ransomware tactics with older extortion schemes: The attacker first steals data and then encrypts it. If a target doesn't pay up, the attackers will leak sensitive documents for blackmail.
"It's increasing constantly, and it's becoming more complex," Basile said. "And if you pay, I've seen [the fact that you paid] resold on the dark web to other attackers, who will hit you because you are known to be an organization that pays."
The coronavirus pandemic -- and the move to remote work for most, if not all, employees -- has caused even more chaos that attackers can take advantage of. Part of the problem is that the typical signals of trust -- being able to talk face to face with someone in the office -- have been disrupted so much by the stay-at-home orders and quarantines, said Errol Weiss, CSO for the Health Information Sharing and Analysis Center.
"Our infosec teams are now working remotely, so they are a little bit more difficult to tap on the shoulder than when they were sitting in an operations center somewhere," Weiss said. "The physical issues of employee locations and dealing with people working remotely is one of the things we are concerned about."
Don't trust, just verify
Fundamentally, in this era of AI-powered cyberattacks and other advanced cybersecurity threats, companies need to take more steps that verify the trustworthiness of users, devices and applications.
Too many companies use a simple username and password to protect data or access, which is clearly inadequate under current conditions. Attackers continue to use a variety of attacks -- from phishing to sifting through breached data to brute-force logins -- to gain access to sensitive systems and data. Deploying multifactor and adaptive authentication across infrastructure and endpoints can help a company make sure their employee is the person behind the keyboard or screen.
"Two-factor authentication does not have to be limited to browser and workstation logins," said Craig Williams, a director at Cisco's Talos intelligence group. "You make them require something extra. Luckily, the deployment of that is pretty well understood right now."
Yet even if a company is using multifactor authentication, their suppliers are often vulnerable. This includes suppliers of security services, according to Michael Hamilton, CISO and co-founder of CI Security, a managed detection and response provider.
"We have seen an uptick in attacks coming to us, trying to penetrate us, to try to get to our customers," Hamilton said. "We have seen the same actor use different techniques. They are using different methods to try and fool us, so this is not some 'rando' who is scanning the internet."
While these attacks have had some success, such as the compromise of Avast's CCleaner in 2017 or the breach of three antivirus firms by a Russian hacker group in 2019, threat groups more often attempt to compromise less tech-savvy services. The Texas ransomware incident, for example, happened because of a breach at a provider of managed services for local governments, Hamilton said.
Making the situation even more critical, the rapid rise in remote working due to stay-at-home orders during the 2020 coronavirus pandemic means that companies have lost visibility into the security of, and threats seen by, their employees. The trust engendered by employees working inside the corporate network is now lost -- and so far, many companies have not replaced it.
"Now that users are at home, we have lost a huge amount of visibility -- the IT and security team may not know where those computers are," TAMUS's Basile said. "They do not have the same level of control over a computer at home as one in the office."
Fight automation with automation
Gaining visibility into activity across a network to stymie the latest generation of AI cyberattacks and other advanced network security threats is made more complex by more remote work, but also by the steady march to the cloud and virtualized or containerized infrastructure.
For many companies, deploying applications to the cloud is done before they have adequate visibility. And to keep up, companies have to automate the analysis of anomalies and response to attacks, said David Martinez, director of cybersecurity for Technologent, an IT services firm.
"There is no single hacking attack in the last 15 years that was not initially automated, so why is our response not automated, but a manual response?" he asked.
Automating analysis and response is a major step in the fight against network threats like AI-powered cyberattacks. Companies also need to automate their identity and access framework, adopting so-called zero-trust principles, said Chris Kubic, CISO for Fidelis Cybersecurity, a provider of security orchestration, automation and response services.

May 1, 2020
Comments